Information and Communication Security Management and Implementation
Description of the information security risk management framework, information security policies, specific management plans, and resources invested in information security management.
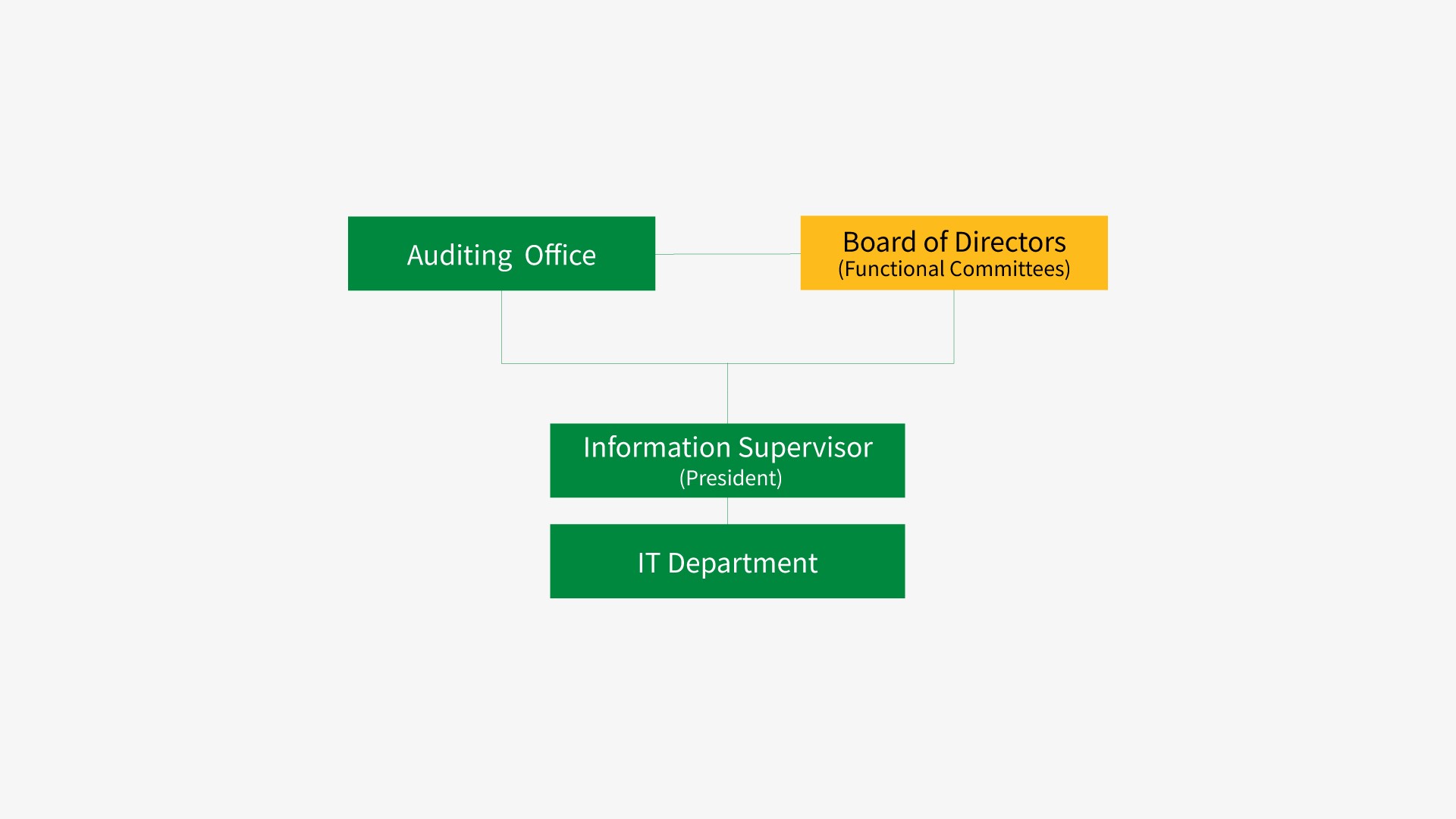
Information Security Risk Management Framework
The Company's IT Department is responsible for information security and regularly reports the operation of information security management to the head of IT. All internal systems are located within the internal network, isolated from the external network to prevent direct access. Multiple network security defense systems are implemented, including front-end firewalls, intrusion prevention and connection screening systems, and secure email management systems, which filter inbound and outbound network traffic to defend against external attacks. These systems can instantly block the latest malware, harmful links, spam emails, and other threats.
Information Security Policies and Specific Management Plans
The Company has established an internal control system for electronic data to maintain its information security policy. Through annual review and evaluation of its security regulations and procedures, the Company ensures their appropriateness and effectiveness. The countermeasures are as follows:
1. Information Security Policy
(1). Ensure the security of the Company's data, systems, equipment, and network communications, and prevent intrusion or destruction from external sources.
(2). Ensure that access rights to system accounts and system changes are processed in accordance with the Company's prescribed procedures and authorization.
(3). Implement destruction procedures to securely dispose of decommissioned computer storage media, preventing accidental data exposure or leakage.
(4). Monitor the security status and activity logs of information systems to effectively manage and respond to security incidents.
(5). Maintain the availability and integrity of data and systems so that operations can be restored in the event of disasters or damage.
Currently, the Company's information security measures are well established. Considering that cyber insurance is still an emerging product involving classification and claims assessment, the Company is still evaluating its future applicability.
(2). Ensure that access rights to system accounts and system changes are processed in accordance with the Company's prescribed procedures and authorization.
(3). Implement destruction procedures to securely dispose of decommissioned computer storage media, preventing accidental data exposure or leakage.
(4). Monitor the security status and activity logs of information systems to effectively manage and respond to security incidents.
(5). Maintain the availability and integrity of data and systems so that operations can be restored in the event of disasters or damage.
Currently, the Company's information security measures are well established. Considering that cyber insurance is still an emerging product involving classification and claims assessment, the Company is still evaluating its future applicability.
2. Information Security Network Architecture
Hosts and endpoints within the internal network are centrally managed with antivirus software, with constant updates to virus definitions and real-time detection of malicious behaviors. This system can intercept viruses, trojans, worms, ransomware, and malicious programs embedded in documents, effectively reducing the risk of damage from hacker attacks.
3. System Account Lifecycle Management and Access Control
User accounts and permissions are assigned based on business scope and job responsibilities. All data access requests must go through an approval process by the relevant responsible managers before use or changes are allowed. When a user leaves their position, their account and permissions are immediately revoked to prevent unauthorized use.
4. Data Access Logging and Archiving
The system is capable of recording and archiving traces of file access, email exchanges, and other related records. Computers slated for disposal undergo hard disk dismantling and destruction to comply with regulatory requirements and the Company's information security policy.
5. Business Continuity for Information Systems
The Company performs local backups daily, weekly, and monthly. Monthly backups are also transmitted to an offsite location for redundancy. Annual system data recovery drills are conducted to ensure the normal operation and security of the information system, reducing the risk of data loss due to unforeseen natural or man-made disasters.
User accounts and permissions are assigned based on business scope and job responsibilities. All data access requests must go through an approval process by the relevant responsible managers before use or changes are allowed. When a user leaves their position, their account and permissions are immediately revoked to prevent unauthorized use.
4. Data Access Logging and Archiving
The system is capable of recording and archiving traces of file access, email exchanges, and other related records. Computers slated for disposal undergo hard disk dismantling and destruction to comply with regulatory requirements and the Company's information security policy.
5. Business Continuity for Information Systems
The Company performs local backups daily, weekly, and monthly. Monthly backups are also transmitted to an offsite location for redundancy. Annual system data recovery drills are conducted to ensure the normal operation and security of the information system, reducing the risk of data loss due to unforeseen natural or man-made disasters.
Implementation Status and Specific Measures for Information Security Management
Monthly IT staff meetings are held to assess overall operational risks in areas such as information security risk management, threat intelligence management, information security controls, outsourcing and dependency management, and incident management and response, to maintain strong network and information security. Currently, the Company's IT staff consists of one IT manager and two IT engineers. In fiscal year 2025, the Company invested NT$1,005,000 to upgrade software and hardware facilities, enhancing information security protection capabilities.